BYOD Demand and Information Security
Glenn Ford
UMBC at Shady Grove
Executive Summary
Having
a BYOD policy without the proper security, device management and
monitoring, and a positive user experience can put the enterprise at
risk. Information can be monitored or leaked, devices and mobile
infrastructure could enter into in an untrusted state, and users become
frustrated and paranoid with the use of their device in the workplace.
If the enterprise fails in their BYOD plan they will be at a competitive
disadvantage for their current workers and ability to hire top talent.
Mobile
security risks as well as threats by agents pose an ever growing and
complicated problem to the information security of a mobile enterprise.
Having the device compromised by authorized or unauthorized users or
resources on the device, man in the middle, or end points compromised
will lead to information being monitored or leaked. Other attacks such
as DoS are at issue as well. Protecting the confidentiality, integrity
and availability of the mobile device and infrastructure is at the core
of mobile security. Mobile device management, monitoring, and user
experience that can work across many platforms and be scalable also pose
challenges. With BYOD users, privacy of the user’s personal assets is a
great concern.
By
providing security through defense in depth there is a known
understanding that any single solution may have vulnerabilities but by
applying layers of security there are levels of redundancy to increase
security. Specific layered security solutions from the moment the device
is turned on until the device is powered off are discussed. Solutions
are discussed for the supply chain and physical security of the device.
Combining the discussed critical solutions in a security policy such as
transient authentication and FIPS 140-2 for data protection, dual layer
FIPS 140-2 encryption for data in transit, and web based non-resident
data only for sensitive information.
With
4 in 10 enterprise level organizations having had a BYOD related
security breach, there needs to be fast response to solving the problems
in the immediate future.
Problem Overview
It
has become apparent that Bring Your Own Device (BYOD) is essential to
the workplace with one report done by Unisys showing 44% of those who
are seeking a job find offers more attractive if they support their
device (Casey, 2012)(1) and according to Campbell (2013)(2), “More than
two-thirds of businesses see boosts in employee productivity and
customer response time [...] and more than half of companies feel they
would be at a competitive disadvantage without BYOD”. The BYOD
phenomenon has even reached to the highest levels of government
security. According to Hoover (2012)(3), "Troy Lange, NSA's mobility
mission manager, said in an interview. ‘This is about bringing
efficiencies and capabilities that people are used to in their everyday
lives and extending that to our national security mission.’”.
The
essential problem that corporate America, the U.S. government and in
fact the world face today is the same. How can enterprises allow BYOD in
the workplace while keeping information secure. When mobile devices
have access to privileged data security policy needs to follow the core
information security principles of: Confidentiality, Integrity, and
Availability (CIA) (Goodrich & Tamassia, 2011, p. 3)(4).
According to Hayes and Kotwica (2013)(5) four in ten enterprise level
organizations have had a security breach related to BYOD. For any
organization to have a successful and secure BYOD environment there are a
number of challenges to overcome (see Appendix A, Figure 1). These
challenges are discussed in more detail in the sections below.
Mobile Security Risks
Some
of the greatest security risks (see Appendix B, Figure 2), as adapted
from National Security Agency (2013, p. 24)(6) include: Voice and
Data-in-Transit (DIT) leaks or monitoring; Malware or Advanced
Persistent Threat (APT) on mobile device or infrastructure; Unauthorized
modification of user equipment or infrastructure; Data-at-Rest (DAR)
unprotected on mobile device; Authentication controls lost or stolen;
Phone number leaked opening up vishing and phishing; disposal of phones
with sensitive information; Denial of services done via battery drain or
other means; Social media applications being used outside the policy of
an organization; Unpatched Operating System, Applications, or Firmware
and unknown vulnerabilities in these; EMI; Eavesdropping techniques such
as Magnetic field coupling or Near Fielding Communication (NFC).
These
risks evolve and change on an almost daily basis. For example it was
recently discussed by Steele (2013)(7) where AirDrop on iOS7 can only be
blocked when the phone is in supervisor mode which currently requires a
physical connection to a MAC. This is a potential new vulnerability for
many phones and MDM environments.
Mobile Security Threats
Dealing
with agents that want to or can attack and harm an organization is
another problem category. Some of the greatest security threats to
mobile security (see Appendix C, Figure 3), as adapted from National
Security Agency (2013, p. 24)(6) include: Attackers from rogue cellular
systems; Modifications to devices hardware or software without
authorization physically, remotely or in the supply chain; Attempted
access to the data on the device, including RAM if was powered on, or
infrastructure from a lost or stolen device; Masquerading as an
authorized user to gain access to the infrastructure; Attackers
attempting to disrupt service or gain access from devices or directly;
Authorized users misuse of privileges; Authorized users attempting to
use unauthorized applications or services; Infrastructure administration
misuse of privileges; Malware masquerading in common applications
installed from untrusted sources.
Device Management
Another
major problem area is management of the device. It is imperative that
an organization have methods in place to handle the problems: Password
protection and reset; Management of mobile attached devices such as
printers; Ability to disable cameras, Bluetooth, Wi-Fi, SMS, and carrier
data connections; Deployment, both local and Cloud or SaaS, with
automated enrollment and provisioning; Wipe of entire device and
selective; Configuration Monitoring and Auditing.
User Experience
With any
solution the user experience is important to have large scale adoption.
Privacy of users in a BYOD environment as Steele (November 8, 2013)(8)
discussed what users expect when it comes to their privacy and the legal
ramifications of companies if not handled properly. Users also expect
their personal data to not be intruded upon and a level of transparency
both in using their personal data and applications as well as privacy
controls used. Performance and transparency to the user are important as
well.
Other Problem Areas
There
are a number of other problem areas besides the listed security risks
and threats, device management and user experience. Other problem areas
that need to be handled include: Reporting capabilities; Scalable
architecture; Service; Integration with PC Management; Platform Support;
Mobility Infrastructure; Cryptographic Key Management System (CKMS);
Overall device performance.
The
ability to secure, manage and monitor enterprise portions of a BYOD and
allow users to have their personal area of the device is a problem.
Information Security and BYOD is the challenge all enterprises,
organizations and countries face. The solutions proposed in this paper
look to merge these nearly polar opposite concepts.
Solutions
The
technology to have a centralized BYOD mobile device management system
that integrates with PC Management is a fast growing sector. There are
many approaches various companies provide. The solutions provided in
this paper don’t look at any particular vendor or solution, rather looks
to provide sets of controls to solve the overarching problem. That is
to allow BYOD to work transparently, efficiently, and securely in an
international, national, and/or enterprise environment without
prohibitive costs.
To
solve the myriad of problems and to continuously be vigilant to
security, as well as the user experience, a proper life cycle solution
needs to be developed. Souppaya & Scarfone (2013, p. 10)(9)
stated there are five life cycle phases: Planning; Development;
Implementation, Operations and Maintenance; Disposal. The guidelines
proposed by Souppaya & Scarfone should be an overarching goal of
the overall management of mobile security in an enterprise. Souppaya & Scarfone (2013, Appendix A)(9) discussed supporting NIST SP
800-53 security controls and publications for enterprise mobile devices
and need to be part of any BYOD policy, procedures, and standards
solution.
Security Policy
There
are many components to planning an MDM solution, a critical piece is
the security policy (Souppaya & Scarfone,2013), (9). Conklin & White (2013, p. 518-525)(10) stated that the security policy,
high level statements by senior management, informs users of the overall
security goals and what security means to the organization. The
security policy also details a user’s obligations and acceptable use.
Privacy is a large concern to all BYOD users. The security policy needs
to cover the user’s privacy and rights in great detail and have
procedures to allow a dual communication channel so that all users feel
involved, thus increasing acceptance and understanding. The security
policy includes what platforms are supported and what level of access
each device may have. It should include statements for how provisioning
and enrollment is handled. It should also cover the administration of
the mobile infrastructure. It will also cover policy updates on all
endpoint devices, servers and infrastructure. The mobile security policy
should work cohesively with the non-mobile security policy. Controls
will include layers of security such as those supported in Hoover
(2012)(3) “Overall, the NSA's mobile security strategy is one of
‘defense in depth,’ Lange said. ‘We understand that any single piece may
have vulnerabilities, but you build in redundancy to increase
security.’”.
Threat Modeling
BYOD
are exposed to more threats than traditional devices such as desktop
computers and doing threat modeling before a design and implementation
will increase the likelihood of a secure environment. Failure to do so
would have development done without knowing all the possible threats.
Rhee, Won, Jang, Chae, & Park (2013)(11) proposed a threat model
method that includes and expands upon ISO/IEC TR 13335-1 and ISO/IEC
15408 with five phases:
- System characterization and analysis of the technical background
- Identifying threat agents
- Identifying assets and classification of value
- Identifying adverse actions and vulnerabilities
- Defining threats.
Proper
threat modeling helps to identify all the security requirements and to
design a BYOD solution and then the incorporation of controls needed to
meet the security requirements.
Secure Boot
From
the moment a device is turned on until OS fully loaded and running is
known as the startup process. During the startup process unauthorized
operating systems and/or software can be loaded in what is one form of
rooting. To prevent this from happening Samsung Electronics Co. (2013,
p. 3)(12) discussed a Secure Boot method that requires the device
bootloader, the kernel and system software to be signed using X.509
certificates with public keys embedded in the hardware of the device
boot loader. Additionally, hardware Read Only Memory (ROM) stores hash
of the certificates. Additional support for another layer of root-trust
is available that can be required by any national or enterprise level,
such as FIPS 140-2 or FIPS 140-3 draft. Securing BYOD devices require a
secure boot solution.
Secure Operating System Kernel
Having
a trusted startup process then relies on the Operating System kernel to
be secure and is the first countermeasure against rooting. The second
vulnerability is in the OS Kernel itself. If there is rooting done on
the kernel, the entire device is compromised. Shabtai, A., Fledel, Y.,
Kanonov, U., Elovici, Y., Dolev, S., & Glezer, C. (2010)(13)
discussed the countermeasure of including SELinux to prevent root level
privileges. It is pointed out that there are certain commands that
cannot be blocked out for the OS to properly function and SELinux can
only deflect and is not an entire solution. Samsung Electronics Co.
(2013, p. 4)(12) explained the introduction of an optimized SELinux for
mobile devices called Security Enhanced (SE) for Android, which was
developed with the involvement of the NSA, to run in an untrusted zone
and Trustzone-based Integrity Measurement Architecture (TIMA) running in
a trusted ARM hardware zone. With TIMA monitoring the integrity of the
OS Kernel, it can run policies such as powering down the device when
integrity violations detected. SE for Android provides more than a first
line of defense on the kernel. It also helps protect confidentiality
and integrity using Mandatory Access Controls to isolate applications
and data into their own contained domains.
Voice over IP (VoIP) Security
Keromytis (2012)(14) discussed the security of VoIP to be classified
into six threat categories as defined by Voice over IP Security Alliance
(VoIPSA): Social threats; Eavesdropping, interception, and
modification; Denial of Service; Service abuse; Physical access;
Interruption of services such as power loss in bad weather. He
aggregated and VoIPSA classified 245 academic research publications with
solutions to one or more of these problems. As part of a comprehensive
security plan, all six threat categories need to be covered in the
non-mobile and mobile security policies and counter-measures. For the
scope of this paper, this section focuses on eavesdropping, interception
and modification.
National Security Agency (2013, p. 13)(6) described using a FIPS 140-2
certified VPN for the outer layer of encryption with an inner TLS tunnel
to a SIP server in the mobile infrastructure and a Secure Real-time
Transport Protocol (STRP) inner tunnel to another endpoint to protect
real time services media streams. All encryptions need to be using Suite
B complaint cryptography with mutual authentication. Performance is an
issue pre-4G but needs commercial upgrades to support proper security.
Key management in SDES-SRTP is covered with mutual authentication using
SIP over TLS.
Reinforcing the above security controls, Keromytis (2012)(14) discussed
in many of the 245 academic papers summaries similar security controls
and provides an exhaustive list of control methods researched and their
pros and cons.
Voice should not be allowed over carrier lines when connected to the
enterprise or organization. SMS have many known vulnerabilities, such as
DoS. Traynor, Enck, Mcdaniel, & La Porta (2008)(15) discussed
exploitations in SMS as it relates to DoS and reference many other
exploitations. Given the many attack threats of SMS, the device
management software should have methods to disable SMS. With BYOD this
is a challenge with mobile device owners and one that each organization
and enterprise needs to address with the device owners.
Data Protection
The
device and its data can have another layer of security using transient
authentication. Nicholson & Noble (2006)(16) proposed transient
authentication such that if the token and mobile device are separated
authentication is broken as constant reauthentication is performed. This
doesn’t replace more traditional authentication, but is rather proposed
as a layer of security for device and data protection. Transient
authentication may be done for parts or all of the data and/or the
device depending on the organization security policies. Using transient
authentication with geo-fencing and/or time fencing security policies
and controls can provide yet another layer of security. Others have
expanded on the concept of Nicholson & Noble, such as Syta,
Kurkovsky, & Casano (2010, January) (17) proposed RFID-AM with
countermeasures for DoS, man-in-the-middle eavesdropping, privacy
concerns such as tracking, deletion, and OTA modifications. Nicholson & Noble(2006)(16) also realized wormhole attacks as a problem
with no good solution at that time. Dimitriou & Giannetsos
(2010)(18) discussed a localized detection and prevention system to help
solve those issues.
Secure Data In Transit (DIT). Keeping
with the layers of security policy, National Security Agency (2013, p.
13)(6) described the outer FIPS 140-2 compliant VPN has the inner
application data encrypted as well with FIPS 140-2 compliant technology
such as AES. Additionally mutual authentication should be performed to
verify identities to help ensure CIA.
Cellular Carrier Networks.
While BYOD is focused on the device in the enterprise, having
protection outside the secure perimeter is necessary. Countermeasures
against rogue base station threats can be done with mutual
authentication in the cellular radio network. Additional security
controls can be placed on endpoint authorization and access.
Secure Data At Rest (DAR). Sensitive
data is containerized and has AES FIPS 140-2 compliant encryption.
Additionally device level encryption should be enforced as well.
Examples of DAT include documents, folders, and email attachments.
Application Level Security
Containerization
of applications to access sensitive data is required. Many commercial
vendors provide this capability, but all vendor products should be FIPS
140-2 certified. Additionally, data sharing, such as copy/paste, must be
prevented or controlled between trusted applications using discussed
security controls for DIT and DIR. Application
containerization/isolation needs to protect data in memory or process
with FIPS 140-2 certified cryptography as well.
Web Based Non-Resident Data
For
even greater security, Shariati (2013)(19) discussed a client server
model similar to the model of a computer terminal. Using a secured
containerized web browser a user would access sensitive data stored only
in the enterprise/organization using DIT security controls. National
Security Agency (2013, p. 14-15)(6) discussed using the web browser with
the outer VPN and inner TLS with mutual authentication and the server
side has all the data and the web client on the mobile device is the
presentation layer only and the server side would have their
authentication controls in place as well with AAA and other means. Both
Shariati and NSA described that the web browser cannot store, cache or
share any data to help ensure information security.
Other
solutions are discussed to be thorough and provide security level
options. By incorporating this solution for all sensitive voice and data
then only security critical information credentials for authentication
to VPN, SIP and Web Server are at risk. If the device is only used for
voice and non-resident data applications then there is no sensitive data
stored on the device thus mitigating attackers having access to any
past voice or data communications. This solution can compliment other
solutions depending Security Policy of the enterprise or organization.
With this solution a lost or stolen device still has risks that an
attacker may be able to gain access but can be further mitigated if
using transient authentication and other countermeasures discussed in
this paper. Additionally, location ability can be put into the firmware
of the device that works with a mobile agent installed at the OS level
that can then be located by proper local and federal authorities.
Further authentication techniques discussed next can provide additional
layers of security.
Authentication
Li,
X., Niu, J., Khurram Khan, M., & Liao, J. (2013) (20) suggested
an improved two-factor smart card authentication process that has
proposed solutions for registration, login, authentication and password
change phases. Also proposed solutions for perfect forward secrecy,
known-key security controls, prompt detection of wrong passwords, and a
user friendly password change mechanism. Mitigation of stolen smart card
devices, insider attacks, replay attacks ,forgery attacks,
server-spoofing attacks, and impersonation attacks. Mutual
authentication and session key agreement is discussed in the solution.
In
the Data Protection section Transient Authentication is discussed as
one layer of authentication security. Protecting access to the device
and applications also requires the use of two-factor authentication for
DoD Directive 8100.2 and the Homeland Security Presidential Directive 12
(HSPD-12) standards. Using certified smart cards, Secure Element SD or
embedded security element chip on the device itself loaded with FIPS 201
certified PIV Applet. This solution can also extend public key
infrastructure (PKI) authentication tools. Additionally storing PKI
credentials on MicroSD cards or using the transient authentication
token.
The
proposed solution is to combine the discussed authentication methods to
provide layers of authentication and strong multi factor
authentication.
Device Tampering
The
supply chain for mobile devices could be compromised, introducing
another possible backdoor attack avenue. Finnegan (December 2012)(21)
discussed Defense Advanced Research Projects Agency (DARPA) proposal for
a program for Vetting Commodity IT Software and Firmware. This program
would have roadmaps to help mitigate threats of backdoors, malware and
other vulnerabilities.
Having
a device stolen or lost could introduce unauthorized modifications to
the device. National Security Agency (2013, p. 10)(6) discussed there
needs to be physical security with tampering seals on all key entry
points into the device. Further physical security for sealing removable
parts such as memory cards into the mobile device is recommended as
well. With BYOD devices there will need to be decisions made in the
security policy on the level of physical security to apply to the
device.
Other Security Controls
There are a number of other layers of security that can be done to help mitigate risks on BYOD devices. Those include:
- Geofencing and time fencing can be another layer of security applied.
- Signature-based Malware Detection.
- Bose, A., Hu, X., Shin, K. G., & Park, T. (June 2008) (22) presented behavioral malware detection framework for mobile devices.
- Firewall
Mobility Infrastructure
The
security of the mobility infrastructure is in of itself an entire
research area, but it is important to discuss a few of the important
security policy goals. National Security Agency (2013, p. 18)(6)
discussed five major areas: Perimeter protection such as firewall,
IPS/IDS; Layered DIT; Exclusive infrastructure for mobile services;
mobile gateways; and Provisioning and Management. The Federal CIO and
Department of Homeland Security (2013)(23) discussed recommendations as
well for security of the mobility infrastructure. Additionally, their
Mobile Security Reference Architecture (MSRA) is an invaluable source
for the entire BYOD and MDM life cycle. Given that the layers of
security rely heavily on encryption, it is imperative the MDM and
infrastructure solution are in accordance with CKMS as discussed in NIST
Draft SP 800-130 (April, 2012)(24).
Device Management
Mobile
device management software has a number of components that include the
security ones discussed, but also monitoring, managing, and support for
the devices. The key areas that need to be addressed include the
following items.
- Deployment options to include local, cloud and SaaS.
- Platform support for as many devices as possible will help a BYOD program succeed. Given many of the solutions proposed, this would require the commercial world to adopt their devices to support proper security controls that are lacking.
- Besides the security solutions for applications and their data already presented, it is desirable to also have the ability to monitor application inventory and usage. A proper application auditing system should be part of the mobile device management solution.
- Document and Content Management. If using data resident security solutions then the device needs to integrate with enterprise document and content management software.
- Network Management to control data usage as to where, when, and if data can be uploaded or downloaded over cellular or Wi-Fi. Roaming cost control would also be part of the network management, as would device diagnostics, usage monitoring and block device access to email or other network access areas if any policy violations occur.
- Service management monitoring and help desk support management.
- PC management integration console standalone and 3rd party tools.
- Reporting system with alerts, response actions to alerts, device and application level analytics. For example, excessive battery drain could be an alert with analytics to determine cause.
- The ability to whitelist or blacklist applications.
- The capabilities to remote device wipe or selectively wipe parts of the device.
- The capabilities to remote lock and locate.
- Able to manage VPN, APN, proxy and gateway settings.
- The ability to disable Wi-Fi, carrier data connections, camera and Bluetooth.
- Manage mobile attached devices such as scanner and printers if physical security allows.
- Configuration monitoring and auditing.
- Automated provisioning and enrollment.
Security, Management, and User Experience
Each
enterprise will have to make decisions on level of security, management
tool capability and user experience. For many problems and necessary
capabilities commercial vendors can provide some of the solutions.
Gartner (May 2013)(25) researched over 100 companies and developed a
Magic Quadrant on 18 qualifying vendors with the following evaluation
criteria: product/service; overall viability; sales execution/pricing;
market responsiveness and track record; marketing execution; customer
experience; and operations. There would need to be the adoption of
solutions that don’t currently exist with vendors.
Conclusion
Without
a well defined BYOD policy enterprises and organizations at the local,
national and international level will be left vulnerable, as well as
mobile device users being left with a feeling of mistrust. Commercial
products do very well at management and operations and do provide entire
suites of security solutions. The challenge is to mash up the best
possible solutions to all the problems discussed in this paper and to
have the forethought to integrate new solutions as other problems,
vulnerabilities and exploitations are encountered. If commercial mobile
device vendors and 3rd party service providers do not find a way to work
closely together to integrate solutions to the security problems of
BYOD then entire nations will be unprepared for an ever growing and
constantly evolving cyber threat.
References
(1) Casey, K. (2012, November 19). 6 Risks your BYOD policy must address.
InformationWeek. Retrieved October 5, 2013, from
http://www.informationweek.com/smb/mobile/6-risks-your-byod-policy-must-address/240142320.
(2) Campbell, S. (2013, January 22). Study: BYOD brings employee productivity gains.
CRN. Retrieved October 4, 2013, from
http://www.crn.com/news/mobility/240146736/study-byod-brings-employee-productivity-gains.htm.
(3) Hoover, J. (2012, February 03). National Security Agency plans smartphone adoption.
InformationWeek. Retrieved October 4, 2013, from
http://www.informationweek.com/government/mobile/national-security-agency-plans-smartphon/232600238.
(4) Goodrich, M.T. & Tamassia R. (2011). Introduction to computer security. Reading, MA: Addison-Wesley.
(5) Hayes, Bob; Kotwica, Kathleen (2013). Bring your own device (BYOD) to work : Trend report. Retrieved November 6, 2013, from http://www.eblib.com
(6) National Security Agency (July 29, 2013). Mobility capability package. Retrieved October 21, 2013, from http://www.nsa.gov/ia/_files/Mobility_Capability_Pkg_Vers_2_2.pdf
(7) Steele, Colin (2013). Blocking airdrop with iOS 7 MDM requires supervised mode.
Retrieved November 9, 2013, from
http://searchconsumerization.techtarget.com/news/2240207123/Blocking-AirDrop-with-iOS-7-MDM-requires-supervised-mode
(8) Steele, Colin (November 8, 2013). BYOD trend in full effect despite privacy, legal concerns.
Retrieved November 15, 2013, from
http://searchconsumerization.techtarget.com/news/2240208754/BYOD-trend-in-full-effect-despite-privacy-legal-concerns
(9) Souppaya, Murugiah; Scarfone, Karen (June 2013). Guidelines for managing the security of mobile devices in the enterprise (NIST special publication 800-124 revision 1).
Retrieved November 4, 2013, from National Institute of Standards and
Technology web site
http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-124r1.pdf
(10) Conklin, WM. Arthur; White, Gregory. Principles of computer security comptia security+ and beyond (exam SY0-301), 3rd Edition. New York: McGraw-Hill.
(11)
Rhee, K., Won, D., Jang, S. W., Chae, S., & Park, S. (2013).
Threat modeling of a mobile device management system for secure smart
work. Electronic Commerce Research, 1-14.
(12) Samsung Electronics Co. (2013). An Overview of Samsung KNOX™ [White paper]. Retrieved
October 26, 2013, from
http://www.samsung.com/global/business/business-images/resource/white-paper/2013/05/Samsung_KNOX_whitepaper_April2013_v1.1-0.pdf
(13)
Shabtai, A., Fledel, Y., Kanonov, U., Elovici, Y., Dolev, S., &
Glezer, C. (2010). Google android: A comprehensive security assessment.
Security & Privacy, IEEE, 8(2), 35-44.
(14) Keromytis, A. D. (2012). A comprehensive survey of voice over IP security research. Communications Surveys & Tutorials, IEEE, 14(2), 514-537.
(15)
Traynor, P., Enck, W., Mcdaniel, P., & La Porta, T. (2008).
Exploiting open functionality in SMS-capable cellular networks. Journal of Computer Security, 16(6), 713-742.
(16) Nicholson, A. J., Corner, M. D., & Noble, B. D. (2006). Mobile device security using transient authentication. Mobile Computing, IEEE Transactions on, 5(11), 1489-1502.
(17) Syta, E., Kurkovsky, S., & Casano, B. (2010, January). RFID-Based Authentication Middleware for Mobile Devices. In System Sciences (HICSS), 2010 43rd Hawaii International Conference on (pp. 1-10). IEEE.
(18)
Dimitriou, T., & Giannetsos, A. (2010). Wormholes no more?
localized wormhole detection and prevention in wireless networks. In Distributed Computing in Sensor Systems (pp. 334-347). Springer Berlin Heidelberg.
(19) Shariati, Behnam. (November 11, 2013). Introduction to cybersecurity 620. Discussion conducted Professor’s Office at UMBC at Shady Grove, Rockville, MD.
(20)
Li, X., Niu, J., Khurram Khan, M., & Liao, J. (2013). An
enhanced smart card based remote user password authentication scheme. Journal of Network and Computer Applications.
(21) Finnegan, Matthew. (December 2012). DARPA concerned over supply chain malware threat. Retrieved November 22, 2013, from http://news.techeye.net/security/darpa-concerned-over-supply-chain-malware-threat
(22) Bose, A., Hu, X., Shin, K. G., & Park, T. (2008, June). Behavioral detection of malware on mobile handsets. In Proceedings of the 6th international conference on Mobile systems, applications, and services (pp. 225-238). ACM.
(23) Federal CIO Council and Department of Homeland Security. (May 23, 2013). Mobility security reference architecture. Retrieved
November 28, 2013, from
https://cio.gov/wp-content/uploads/downloads/2013/05/Mobile-Security-Reference-Architecture.pdf
(24) Barker E. , Smid M., Branstad D. & Chokhani S. (April 2012). A framework for designing cryptographic key management systems (NIST special publication draft 800-130).
Retrieved November 4, 2013, from National Institute of Standards and
Technology web site
http://csrc.nist.gov/publications/drafts/800-130/second-draft_sp-800-130_april-2012.pdf
(25) Gartner. (2013, May 23). Magic quadrant for mobile device management software. Retrieved November 23, 2013, from http://www.gartner.com/technology/reprints.do?id=1-1FRG59X&ct=130523&st=sb
Appendix A
Figure 1. Bring Your Own Device Mobile Device Management Problems Overview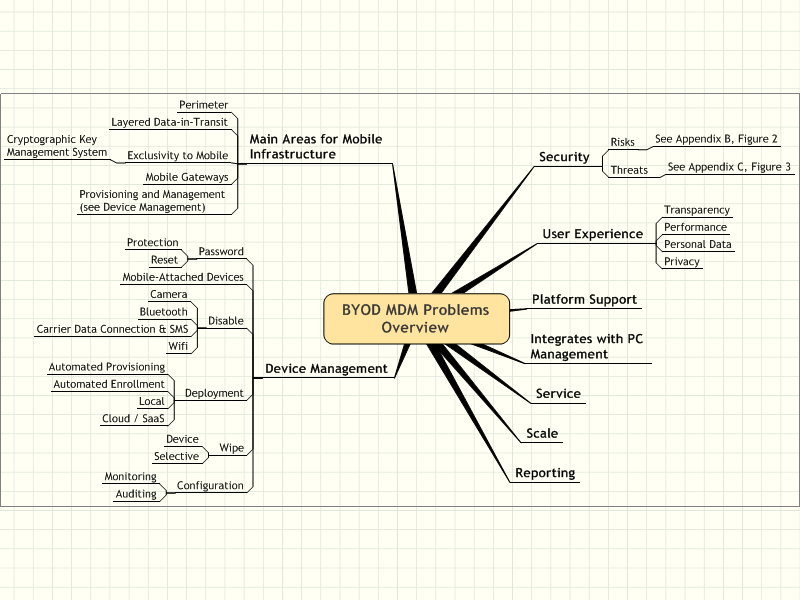
Figure 1.
This diagram provides a quick reference of the problems facing BYOD
device management. The security risks and threats problems are provided
in separate figures.
Appendix B
Figure 2. BYOD MDM Security Risks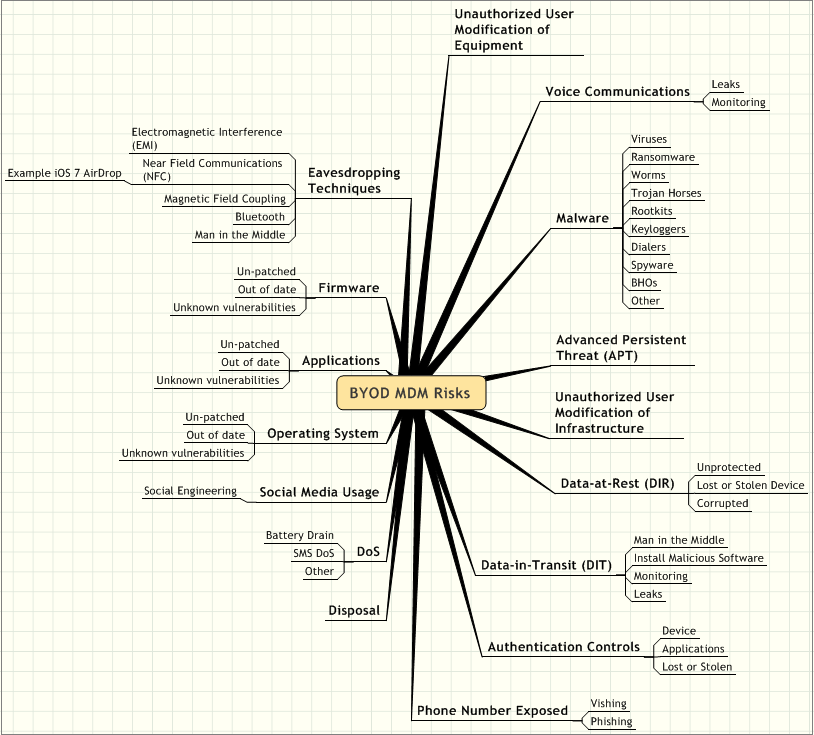
Figure 2. This diagram provides a quick reference of BYOD MDM risks enterprises and organizations face today.
Appendix C
Figure 3. BYOD MDM Security Threats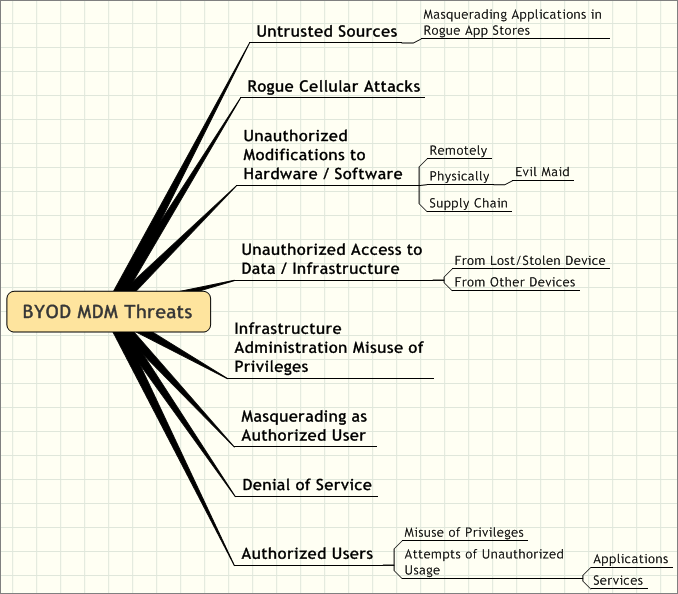
Figure 3. This diagram provides a quick reference of BYOD MDM threats enterprises and organizations face today.
No comments:
Post a Comment