My notes on this paper: Our group was assigned with developing a security plan for a fictitious company. We were not to worry about budget, but were asked to be as comprehensive as possible in the given maximum paper length. This is not a research paper so there are no citations/references except a few exceptions where we quotes ideas from our professor for this project. I'd love to hear feedback from you so please post a comment, email or tweet me. --Glenn Ford
AMG Enterprise Security Plan
Glenn M. Ford, Aaron S. Cameron, Michael J. Park
UMBC at Shady Grove
Executive Summary
AMG Enterprises is an American owned e-commerce company headquartered in Rockville, Maryland. As a company with sales in 22 countries, annual revenue of $61 million (U.S.) in 2012, 97 employees and patents and other intellectual property, AMG is under constant attack by criminals and other hackers. Protecting employees, facilities, equipment and data offers a myriad of challenges. The Confidentiality, Integrity and Availability (CIA) of AMG information is critical to the continuity of operations and to the trust placed in AMG by their customers and vendors. AMG has a comprehensive security plan and has implemented policies, procedures, countermeasures and the operational model of security to ensure the protection of all company assets, as it pertains to physical, network, operational, personal and wireless security. AMG’s headquarters was custom built with security as a top priority. AMG’s policies were drafted to ensure security throughout all aspects of operations. No expense has been spared in deploying countermeasures to meet all threats both now and in the foreseeable future.
Problem Overview
As an ecommerce online business, AMG has an online reputation and brand recognition to maintain. If this reputation is tarnished company growth can be severely degraded. Our customers have complete confidence and assurance that AMG is providing quality products, customer service, and security of all client information.
At the center of this problem is protecting the CIA of AMG Enterprises assets. These assets include: online reputation; brand recognition, client and company information, buildings, inventory, hardware, proprietary software, personnel and overall organizations information technology (see Information Technology Organizational Chart, Appendix G, Figure 1). The cybersecurity threats of data breach and/or threats, denial-of-service (DOS) attacks, insider theft of intellectual property, deliberate corruption of electronic files from hacker attack or malicious attacks including worms and other means are all security problems this document hopes to solve with security policies, procedures and standards and the Countermeasure Triangle (The People, Policy, Technology Triangle; see Appendix H, Figure 2).
Security Policies
AMG’s security policies section provides broad statements that outline what security means and AMG’s goals for security. The term employee in this document refers to all AMG staff and contractors.
Operational Security Policy
Policy Lifecycle. AMG’s policy lifecycle is divided into 4 sections as it pertains to security policies and countermeasures.
- Plan. Develop or modify policies, procedures, guidelines, and security components.
- Implementation. Implement plan and include an instruction period for those who are affected by the change or introduction of the new component.
- Monitor the Implementation. Monitor to ensure security components are effective in securing assets.
- Evaluate the effectiveness. Evaluate security measures using vulnerability assessments and penetration tests to ensure security is adequate.
Operational Model of Security
There was a time when prevention was thought to equal protection; however assets are left unprotected when prevention fails. Therefore, AMG requires measures to detect failures and methods to address the problem. Thus, the security equation is: Protection = Prevention + (Detection + Response).
Change Management Policy
Proper procedures will be followed when modifications to IT infrastructure are made, and such changes will only be made by authorized personnel. Decisions to make any modifications/changes will only be made by the Chief Technology Officer. Requests for modifications/changes can be submitted to the CTO by any department head. The CTO will assign personnel responsible for implementing said modifications/changes. All modifications/changes will be reviewed and tested in secure R&D area prior to public release. All modifications/changes and test results will be documented and will need to be approved by the CTO before public release.
Classification of Information Policy
All corporate information must be classified into one of four categories based upon the importance and value to the company. The four categories are: Publicly Releasable; Proprietary; Company Confidential; For Internal Use. Each classification level must cover each of the following issues:
- How it is protected
- Who may have access
- Who has authority to release it
- How it should be destroyed
All employees will be properly trained in procedures they have authorization to access. All four levels of classification will use Mandatory Access Controls (MAC), Role and Rule Based Access Controls to identify who may have access to what resources. Smart cards also identify classification level.
Acceptable Use Policy
Employees will be properly trained on the appropriate use of company resources including email, internet access, and computer systems. The AUP will clearly delineate activities that are not allowed such as personal business and installing software. Statements will be accompanied with penalties if the policy is ignored. This will maximize employee productivity while minimizing organizational liability. Policy will detail responsibilities to protect company assets. AUP will work with legal and include statements on monitoring employees’ use of computers and network. A banner will be included on all login screens.
Internet Usage Policy. The policy will address which sites employees are allowed to visit, and not allowed to visit. It will also define what they are not able to post on social media sites in regards to their work.
Email Usage Policy. Employees will be restricted to using email for official use only. The policy will also define types of messages that are inappropriate to send to coworkers. Specific disclaimers must be attached to individuals emailed outside of the company.
Due Care and Due Diligence
All AMG employees are expected to exercise due care, the standard of care a reasonable person is expected to exercise in all situations. AMG is expected to exercise due diligence, the standard of care AMG is expected to exercise in preparation for a business transaction.
Due Process Policy
The HR department will work closely with AMG legal to ensure that AMG policies as it relates to the rights of employees are keeping the current laws and regulations at local, state and national levels. All employees will be guaranteed fairness, justice and liberty as it relates to their legal rights.
Need to Know
Need to know works in tandem with least privilege. Least privilege limits employees to the minimum privileges and information they need to perform their job. Need to know ensures they have a justified reason to access the information. Therefore an employee must always have the appropriate authorization and need to know, to access a piece of information.
Disposal and Destruction Policy
All confidential physical and electronic records that are no longer required for operational use, for compliance purposes, or as part of an internal or external investigation, will be destroyed in a manner that will leave them irretrievable.
Service Level Agreements Policy
AMG Corporate Legal will work with executive management and service providers to develop Service Level Agreements (SLAs) that ensure there is no interruption in AMG business continuity and proper disaster recovery is included. The SLAs need to clearly define policy, procedures and standards for services and support provided. Corporate Legal and Executives must be involved in all SLA contracts. Services Security Policies must match up with AMG Security Policies as negotiated by AMG executives and Legal. This includes, but not limited to, all Commercial Off-The-Shelf (COTS) products, IT as a service (ITaaS), and Software as a Service (SaaS) used by AMG. COTS, ITaaS and SaaS will use mutual authentication when possible. SLAs will also include penalty clauses for failure to comply.
Authentication Policy
AMG policy requires to critical areas requires security access using smart card and pin number or token and pin number. Multi-factor authentication is required for all access. Pin numbers must be eight numbers and be a random sequence. Employees are trained to not use pin numbers easily social engineered, such as birthdays, phone numbers, and street addresses. All pin numbers must be changed every 90 days from a control center administered by security staff. Some devices, such as computer BIOS or 3rd party hardware/software, may not support this. In those instances a strong password of 13 characters or more must be used. It must be a combination of lower case, upper case, numbers, and special characters. As with the pin number, no password should be possible via social engineering. No use of names, dates, or other such patterns can be used.
Human Resource Policies
Employee Hiring and Promotions. AMG utilizes a comprehensive approach to hiring, requiring drug tests, background checks depth based upon classification level, verification of education credentials, confirmation of past work history, and reference checks. Employees must sign contract to protect confidential or higher information with penalty clauses. When an employee is promoted HR and security will review the promotion and determine if the employee needs additional access privileges. A User ID is provided during employment with assigned smart card, token and pin numbers. First 30 days employees have limitations placed via MAC, Role and Rule Based Access Controls Company wide.
Demotion, Retirement Separation or Termination. If an employee is demoted classification access will be reviewed and access controls adjusted accordingly. When an employee is separating from AMG by choice, AMG will consider limiting their access to information. Such a determination will be made by the employee’s department head. When an AMG employee is terminated, all access will be revoked immediately and said employee will only be permitted to remain on premises long enough to collect personal belongings.
Mandatory Vacation Policy. All employees of AMG are required to take mandatory vacation that spans a minimum of 4 work days and 6 calendar days. All mandatory vacations need to be coordinated with the employee’s supervisor to ensure that there is another staff member available and properly trained, certified and/or competent to do the work duties of the employee on leave.
Job Rotation. AMG will occasionally rotate employee’s job functions to foster a better understanding of AMG’s business. A secondary benefit is increased security awareness across the company.
Aspects of Security
This section will use the Operational Model of Security for Physical, Network, Information, Personal and Wireless Security. The Information Security section is broken down into two subsections: Host Security and Securing Applications.
Physical
The Physical Operational Model of Security (see Appendix A, Table 1) provides a quick view of topics covered in this section. The Physical Security Top Floor Diagram (See Appendix I, Figure 3) and Physical Security Bottom Floor (See Appendix J, Figure 4) provide additional overview.
Prevention. AMG’s buildings are set back from roads and sidewalks and surrounded by planters and fences. Construction surveillance technicians with appropriate security clearance monitored all aspects of building construction to prevent the installation of eavesdropping equipment. All buildings have two access points: a main employee/visitor entrance and a loading dock which are both manned by armed guards with access logs and equipped with 8’ tall turnstiles. Outside each loading dock is a guard posted at a traffic control barrier with a list of pre-authorized deliveries. No visitor will be granted access to building without an AMG employee with escort authority claiming responsibility for the visitor. Biometric scanners, smart card and pin numbers are required to gain access to most secure areas of building, such as the data center and research and development (R&D). Additionally, separations of duties system will be required to gain access to these areas, which are both located in the middle of the top floor of the building and have drop ceilings. Servers are kept in locked cabinets. A guard is posted outside the entrances to these areas. All cell phones and other electronic devices are checked in with guard and not allowed in secure areas. HVAC system keeps building at constant temperature. Surge protectors are utilized. TEMPEST approved equipment throughout building. Guard supervisors conduct regular post inspections to ensure guard readiness and functionality of equipment. Security specialists conduct regular maintenance of security equipment. Regular penetration testing is conducted to ensure readiness of security perimeter and effectiveness of procedures. A service-level agreement is in place between AMG and security guard contracting company. SLA states guard force must follow General Orders and Post Orders, which detail every aspect of what is expected of guards. Guards are on duty 24 hours a day, 7 days a week.
Detection. The perimeters of all AMG facilities are monitored by CCTV. Security Control Center (SCC) personnel monitor CCTV system, which is on its own network, from the center of each building’s basement. Roving guards will patrol the outside and inside of buildings looking for any suspicious activity, unattended packages, unsecured classified materials, etc. Fire detection system is placed in every room, hallway, and stairway every level. All AMG personnel and visitors will wear properly displayed badges at all times in and will be challenged by guards when seen without them. Detailed logs are kept of everyone who badges in and badges out of building. Smart cards and pin numbers are required to gain access to all offices, suites and utility closets so access logs are kept there as well. All access logs are accessible from the SCC.
Response. Roving guards are available to immediately respond to security/medical/fire incidents after being dispatched by SCC personnel. Fire suppression system is located in same general rooms as fire detection. Fire extinguishers are provided in all critical areas. Uninterruptible power supply is utilized along with backup generators.
Network
The Network Operational Model of Security (See Appendix B, Table 2) provides a quick view of topics covered in this section.
Prevention. AMG utilizes RSA’s FraudAction to protect against phishing, pharming, trojans, and rogue apps. AMG has a primary and secondary office with the same network architecture. IPSec is configured in tunnel mode to facilitate confidential communication between offices. IPSec routers are configured as host to host and gateway to gateway which act as proxies for end devices, ESP and AH protocols will be blocked except from specific internal addresses. IPSec utilizes HMAC-SHA1 for integrity and authenticity, and AES for confidentiality. AMG also utilizes Verizon’s cloud security which helps scan emails for malicious content, and protect against Denial-of-Service (DoS) attacks and Distributed DoS (DDoS) attacks (See Network Topology Overview, Appendix K, Figure 5). Cloud security is used in conjunction with the anomaly-base active NIDS. Inside each building the initial line of defense is the DMZ. The DMZ first uses a basic packet filtering firewall configured to block TCP, UDP and ICMP by default. Opening specific services and ports by approved and authorized change management policy and procedures is required. Web servers and firewalls will be hardened to run only the services and applications required to perform its job using implicit deny. Proxy servers will allow internet content filtering and provide an extra layer of security. Traffic attempting to enter the intranet from a DMZ server must then pass through the internal stateful packet filtering firewall. Behind the internal firewall is an inline IPS that can react appropriately to malicious network traffic. Intranet departments are grouped by VLANs through trunking which allows security personnel to easily maintain and administer the network. Instant messaging services have been disabled as a security precaution. All ethernet ports are also disabled by default to prevent users from connecting unauthorized end devices. A network and system administrator must enable the ethernet port for use. Phone lines are provided with VoIP, which travels through all the prevention measures. Remote access via VPN using L2TP in conjunction with IPsec provides confidentiality, integrity and authentication. Users will be required to log in to the network with their PIN and token as an added layer of security. All laptops are company provided with patch management software performed over the VPN with vulnerability scanning and all host security measures enabled with the additional security of entire disk encryption. See Appendix L, Figure 6 for a diagram of the AMG Network Topology logical layout.
Detection. An active network anomaly based IDS (NIDS) resides within the DMZ and is used in conjunction with cloud based mitigation. When it recognizes malicious traffic it immediately stops communications for 24 hours and alerts security personnel. A honeynet is also present within the DMZ, it is a collection of many honeypots that simulate our network environment. A potential attacker will be directed to the honeynet where they can be contained and monitored. Inside the intranet each department has an active host based IDS to scan inbound and outbound traffic on individual end devices. Like the active NIDS, the HIDS are able to temporarily stop malicious activities while notifying security personnel for further action. Regular penetration tests, that include vulnerability assessment and scanning, will be performed and adjustments will be made as necessary.
Response. Forensics is performed and depending on the severity of the incident, security personnel are able to shut down portions of the network to contain and prevent further damage. Data is classified within the system and protected appropriately. A protocol analyzer lies directly behind the internal firewall. During incident response it’s used to capture and decode network traffic and look for evidence of botnets, trojans, and infected systems.
Information Security
Host Based Security. All servers are enterprise level Linux systems with SLAs for support response time, level of support and remediation well defined. All laptops and desktops are Macintosh based with SLAs for support response time and level of support well defined. This section details security once an individual has physical (at console) or logical access (at login prompt thru Secure Channel such as SSH or Remote Desktop). The Host Based Operational Model of Security (See Appendix C, Table 3) provides a quick view of topics covered in this section.
Prevention. All preventive measures are required in order to protect the hosts properly. Those minimum standards are as such:
- Double Authentication - Hosts will require a smart card and personal PIN with Kerberos. Remote Login, for the few cases even possible, uses RSA + 8 digits pin with Kerberos. .
- Bios Locked - No Host can have its boot sequence altered and the BIOS have Mandatory Access Controls with strong password authentication to access.
- Patching - All hosts will have random patching cycles every 5-9 days for OS and installed applications. Some patches are more critical and may come at different intervals.
- Host Firewall and Antivirus (AV) - Corporate AV Software must be up-to-date and running at all times. AMG AV includes host level firewall for layered defense. AV also detects man in the middle devices installed on hosts.
- Implicit Deny Services - All ports are closed unless specifically requested and approved.
- USB / External Media Disabled - All USB and external media devices are disabled and not allowed. All computer ports have physical locks.
- Least Privilege - Following the overall security policy of Least Privilege is true for access control on all Hosts.
- Access Control - MAC, Rule and Role based access to control which Hosts employees can access.
- Media Access Control - All devices have registered MAC address for network layer security.
Detection. All hosts will include system, service, user and application level audit logs. Security Teams will be monitoring the audit logs on a daily basis. There is also a user agent on all host machines to provide real time monitoring for internal or external threats All hosts will also have port scans done at random time periods to verify proper protections were implemented and that no backdoor has been opened. Nightly incremental backups and weekly full backups of all hosts are performed with real time replication to mirror site. Host Based Intrusion Detection System (HIDS) is required to dynamically monitor if anything or anyone from an external or internal source is trying to circumvent the systems security policy. Penetration tests will be performed randomly and weekly on all hosts to verify all patches, hardening, etc has been done for all known vulnerabilities.
Response. In the case of a host being compromised, an Incident Response Team will physically remove and take the host to a private segmented network to perform forensic analysis. Depending on the nature of the problem the host may need to be wiped and rebuilt. Hosts can be restored from a known good backup date and time.
Securing Applications. All web applications should follow all corporate policies and the securing applications operational model of security (See Appendix D, Table 4). The Least Privilege, which is a company wide Security Policy, is a central focus in this section. Web application R&D is done on a private VLAN that has a systems development life cycle (SDLC) with proper testing before moving to public servers.
Prevention. All preventive measures are required in order to properly secure applications. Those minimum standards are as such:
- Input and Data Validation - Input should not be trusted and validations on all input and data should be performed. This includes, but not limited to length, range, format and type. Constrain, reject and sanitize input to allow known good data, reject bad data and make potentially malicious data safe.
- Authentication - Follow corporate strong password policies for all web applications. Passwords stored using latest SHA-3 with no plaintext over the networks. Separation of anonymous and authenticated pages. Secure authentication tokens with encryption (AES) and secured communication channels. Use layered defense.
- Authorization - Use least privilege on all accounts and consider granularity of access. Enforce separation of privileges. Use multiple gatekeepers using IPsec policies for host restrictions server to server. Secure system resources against system identities using need to know.
- Configuration Management - Use least privileged services accounts and separation of administrative privileges using role-based. Secure configuration stores using ACLs. Secure administrative authentication using certificates, mutual authentication and IPSec and if critical disable remote.
- Sensitive Data - Do not store secrets if at all possible, and use SHA-3 if user knows secret. Secrets include passwords, database connection strings, and credit card numbers. Provide privacy through AES encryption and use message authentication codes (MAC) for integrity. Use Mutual Authentication with client and server. Retrieve secrets only on demand, decrypt it, use it and discard. Use SSL/TLS for client and web server and IPSec between servers. Intermediary use SOAP with message level encryption.
- Session Management - Use SSL/TLS to protect session authentication. Limit session life to reduce hijacking and replay attacks and use session tokens. The web application to session state store network link uses IPSec.
- Cryptography - As mentioned in the other countermeasures all encryption uses the strongest possible keys using combination of AES, RSA and SHA-3 for hashing. All keys should be cycled on a regular basis.
Detection. Using the listed detection methods will help mitigate potential attacks.
- Penetration Testing - Use attack simulations to test security controls implemented.
- Application Monitoring - User account lockouts if account under attack and monitoring tools for unusual activity using a proactive approach.
- Exception Management - When problems arise do no leak/expose information to the client and log properly. Don’t log secrets. Catching exceptions properly to not leave application in a vulnerable state and also helps against DoS.
- Audit Logs - These are also encrypted, backed up and analyzed frequently.
Response. The following countermeasures will help in security. Incident Response Teams will be properly prepared and when an incident is flagged properly identify the problem as a security issue. The team will contain the problem and determine what has been affected and disconnect to prevent further spread any resources required. The team will do forensics to discover the origin of the incident and eradicate. Using backups restore to a proper known good state and evaluate the problem to prevent from happening again.
Personal Security
One of the most common ways security is breached is through people, either by accident or maliciously. AMG employees need access to information and other resources to do their jobs and thus there is the potential to abuse the access privileges they have. This section will discuss the Personal Operational Model of Security. See Appendix E, Table 5.
Prevention. All preventive measures are required in order to secure the applications properly. Those minimum standards are as such:
- Employee Training - People are one of the most attacked avenues by hackers. As mentioned in the Human Resources Policies, making sure new employees receive proper training and existing employees have quarterly refresher training is essential to good security. Social Engineering is a big area of the training and should include training and tests in the following topics: Data Aggregation, Phishing, Spear Phishing, Whaling, Shoulder Surfing, Vishing, SPAM, Reverse Social Engineering, Hoaxes and Piggybacking and Road Apples. All employees will be tested and assessed.
- Job Rotation - To help everyone have better understanding and also to help ensure multiple employees are properly trained at any given task.
- Separation of Duties - By dividing tasks up or in critical information areas even requiring two people to gain access or perform a task for additional security. This helps ensure no single individual can abuse the system for his or her own gain.
- Least Privilege - Only the necessary rights and privileges are granted to an individual to perform their task with no additional permissions. This will also include implicit deny and need to know measures.
- Mobile Device Management (MDM) - All MDM devices used must be provided by the company and can only be used for company business. No company information/data will be on the devices, encryption for all components (sms, email, internet, and data) will be in the container. No other applications other than company provided are allowed on the device.
- Travel - It is important that all people traveling are aware of the network they are using. Only hard lines should be used, no wifi in hotels, airports, etc. Using MDM provided equipment and encryption to send/receive email, etc.
- Two Person Authentication - As mentioned in Separation of duties, some critical areas of the company will have two person authentications.
- Login Banners - To remind the user of their rights and responsibilities a banner is displayed prior to any connection to company resources.
- Employee Responsibilities - Individuals are responsible for helping keeping a secure environment by having : Locked door/office/cabinets/etc; No sensitive data in your car unprotected; Secure Storage media devices in a secured device; Shred paper containing organization information prior to discarding; Do not divulge information including other employees not authorization ; Do not discuss with family members; Protect laptops with regular updates, scans and use encryption; Use company provided laptops only for company work, not personal use; Be aware of who is around you when discussing sensitive information from eavesdropping; Enforce corporate access control procedures; Be aware of proper procedures to report suspected or actual violations of security policies; Follow procedures for proper password security practices.
Detection. Using the listed detection methods will help mitigate potential attacks.
- Audit Logs - Security team(s) will perform daily inspection of audit logs.
- Employee Awareness - Having staff be able to know an email or phone call is social engineering then report it properly.
- Penetration Testing - Passing a written test on social engineering and other security policy is a first step. Simulating personal security attacks to test the level of testing and awareness that staff has. Evaluating and fixing policies and procedures where shown vulnerable is essential.
- Activity Monitoring - Employee activity can and will be monitored through automated and manual processes.
Response. Once there is a suspected failure in personal security policies and/or procedures an Insider Incident Response team is assigned to investigate and assess the problem. Isolating the affected resources as quickly as possible to mitigate further damage is essential. The main strength in response will be through a corporate culture of family and team. People are also the greatest strength in security and AMG employees working together can mitigate security issues by reporting anything suspicious. Nothing is too small to report.
Wireless
The Wireless Operational Model of Security (See Appendix F, Table 6) provides a quick view of topics covered in this section
Prevention. AMG has a separate “internet only” network setup with no connection to company servers. AMG offers wireless access to this network as a perk for employees who wish to access from their personal devices while on personal time. The router uses WPA2 encryption. Router firewall enabled and blocks TCP, UDP and ICMP by default. SSID broadcasting is disabled. Only devices with registered MAC addresses will be granted access to network. All devices must have a corporate scan and security agent installed prior to being granted authorized access. The router is placed in the center of the upper floor of the building where the majority of personnel work. The wireless signal does not extend to the bottom floor or outside the building. A strong password: a long, randomized string of numbers and capital and lowercase letters is used to access the router configuration, and this is only available to network administrators. A separate wireless password is provided to employees for access to the wireless network connection. This password changes every 90 days.
Detection. AMG employs a Network Intrusion Detection System on the “internet only” network.
Response. Incident response teams in place.
Appendix A
Table 1
Physical Operational Model of Security
Prevention
|
Detection
|
Reponses
|
Set Back from Road/Sidewalk
|
CCTV
|
Roving Guards
|
Surrounded by Planters and Fence
|
Roving Guards
|
Fire Suppression System
|
Construction Surveillance during Construction
|
Fire Detection System
|
Uninterruptible Power Supply
|
Only Two Access Points
|
Detailed Access Logs
|
Backup Generators
|
Armed Guards & Turnstiles
| ||
Traffic Control Barrier
| ||
Visitors Require Authorized Escorts
| ||
Biometrics, Smart Cards, Pin Numbers, Separation of Duties Required to Access Most Secure Areas
| ||
Regular Post Inspections of Guards
| ||
Regular Penetration Testing
| ||
SLA Between AMG and Contracting Guard Company
| ||
TEMPEST
| ||
Surge Protectors
| ||
Drop Ceilings
| ||
Guards Posted 24/7
|
Appendix B
Table 2
Network Operational Model of Security
Prevention
|
Detection
|
Response
|
IPSec
|
Network Intrusion Detection System
|
Incident Response Teams
|
Firewalls
|
Host Intrusion Detection System
|
Protocol Analyzer
|
Tunneling
|
Honeypots
|
Redundancy
|
DMZ
|
Honeynets
|
RSA FraudAction
|
Packet Filtering Capabilities
|
Penetration Testing
| |
Proxy Server
|
IDS/IPS Manager
| |
Encryption
|
RSA FraudAction
| |
Hardened Servers
| ||
Ethernet Ports Disabled
| ||
IM Disabled
| ||
VPN for Remote Access
| ||
Authentication
| ||
Verizon Security Products
| ||
RSA FraudAction
|
Appendix C
Table 3
Host Based Operational Model of Security
Prevention
|
Detection
|
Reponses
|
Double Authentication
|
Audit Logs
|
Incident Response Team
|
Bios Locked
|
Port Scans
|
Backups
|
Patching
|
Host Based Intrusion Detection System (HIDS)
| |
Host Firewall / Anti-Virus
|
Penetration Tests
| |
Implicit Deny Services
| ||
USB / External Media Disabled
| ||
Least Privilege
| ||
Access Control
| ||
Media Access Control
|
Appendix D
Table 4
Securing Applications Operational Model of Security
Prevention
|
Detection
|
Reponses
|
Input and Data Validation
|
Penetration Testing
|
Incident Response Team
|
Authentication
|
Application Monitoring
|
Backups
|
Authorization
|
Exception Management
| |
Configuration Management
|
Audit Logs
| |
Sensitive Data
| ||
Session Management
| ||
Cryptography
|
Appendix E
Table 5
Personal Operational Model of Security
Prevention
|
Detection
|
Reponses
|
Employee Training
|
Audit Logs
|
Incident Response Team
|
Job Rotation
|
Employee Awareness
|
Employee Reporting
|
Separation of Duties
|
Penetration Testing
| |
Least Privilege
|
Activity Monitoring
| |
Mobile Device Management
| ||
Travel
| ||
Two Person Authentication
| ||
Login Banners
| ||
Employee Responsibilities
|
Appendix F
Table 6
Wireless Operational Model of Security
Prevention
|
Detection
|
Response
|
Internet Access Only
|
Network Intrusion Detection System
|
Incident Response Teams
|
Strong Passwords
| ||
Frequent Password Changes
| ||
WPA2
| ||
All devices must register MAC addresses
| ||
Security Agent
| ||
Proxy Server
| ||
Firewall Enabled and Blocks TCP, UDP and ICMP
| ||
SSID Broadcast Disabled
|
Appendix G
Figure 1. AMG Information Technology Organizational Chart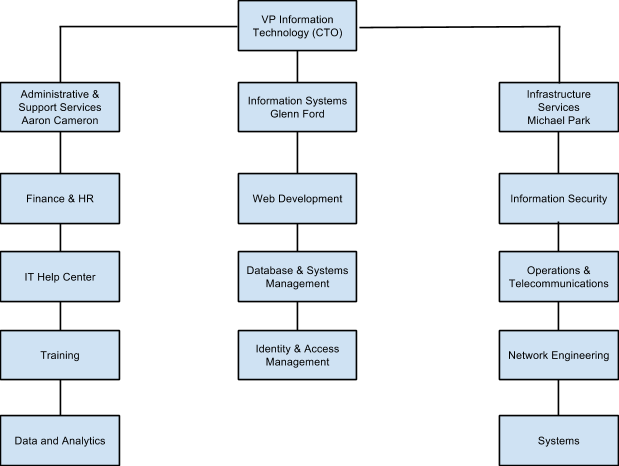 Figure 1. This figure illustrates the Information Technology Organization for AMG.
Figure 1. This figure illustrates the Information Technology Organization for AMG.
Appendix H
Figure 2. The People, Policy, Technology Triangle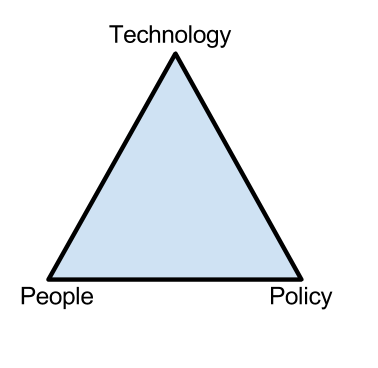
Figure 2. This figure illustrates the security relationship between people, policy and technology. Shariati, B. (Introduction to CyberSecurity Lecture, September 23, 2013). Organizational Security. Lecture conducted from UMBC at Shady Grove, Rockville, MD.
Appendix I
Figure 3. Physical Security Top Floor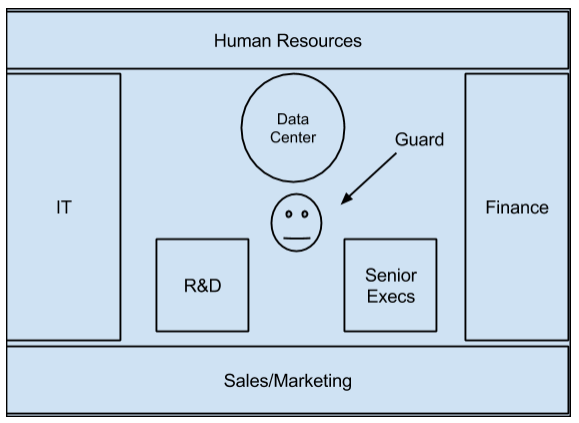
Figure 3. The top floor of AMG building shows locations of various vital areas of the company.
Appendix J
Figure 4. Physical Security Bottom Floor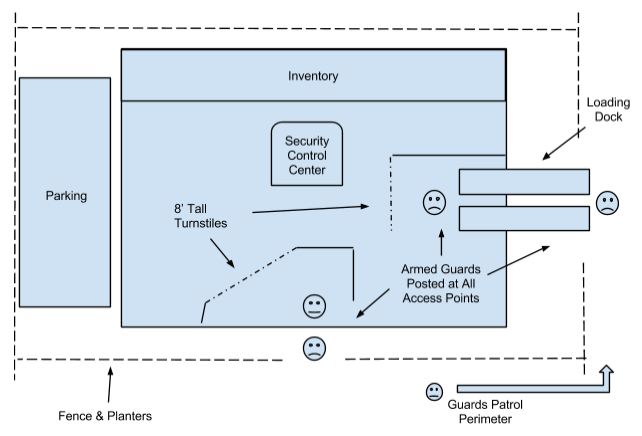
Figure 4. The bottom/ground floor of the AMG building shows physical security inside and outside the building.
Appendix K
Figure 5. Network Topology Overview
Figure 5. An overview diagram of AMG’s network topology shows the main and secondary office.
Appendix L
Figure 6. AMG Network Topology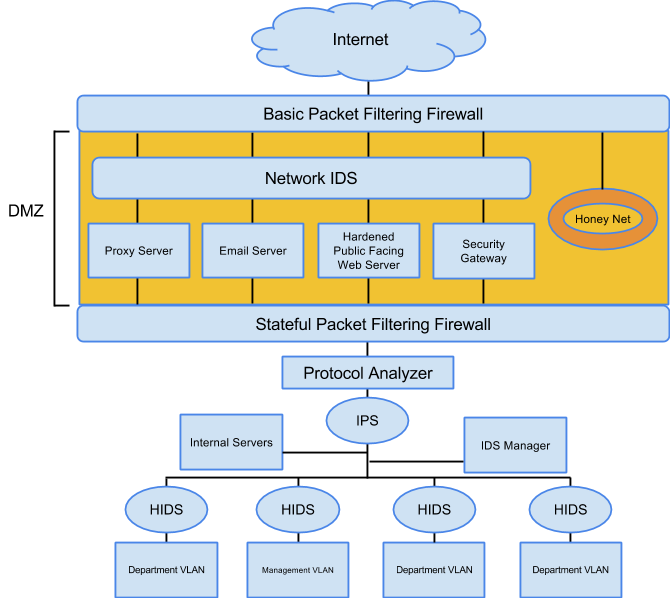
Figure 6. Figure represents a deep dive of AMG’s network topology in the main and secondary offices.
No comments:
Post a Comment